There is a new kid on the block in Computer Virus terms and it has been making a lot of news headlines recently. WannaCry is the latest in a trend that has been on the rise over the last couple of years.
Naturally this raises many questions.
A NEW BREED OF COMPUTER VIRUS
Many of us at Infotex have been in the industry long enough to remember the early days of experimental viruses that were written as a side project to demonstrate the authors expertise and in general not intended to cause mass damage e.g. the Melissa and Nimda worms from early 2000’s.
Sadly this all changed when CryptoLocker was released in 2014. The positive motives of authority and experimentation were replaced by greed and now crime. Suddenly someone had discovered that by encrypting (effectively password protecting) the victim’s documents people could be extorted to pay in order to regain access. By coupling this to the Bitcoin anonymous virtual currency there was a way to extort money without being traced or blocked by law enforcement – a perfect opportunity for the bad guys.
WHAT’S SO SPECIAL ABOUT WANNACRY?
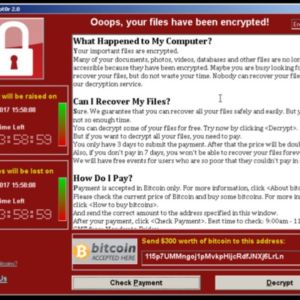
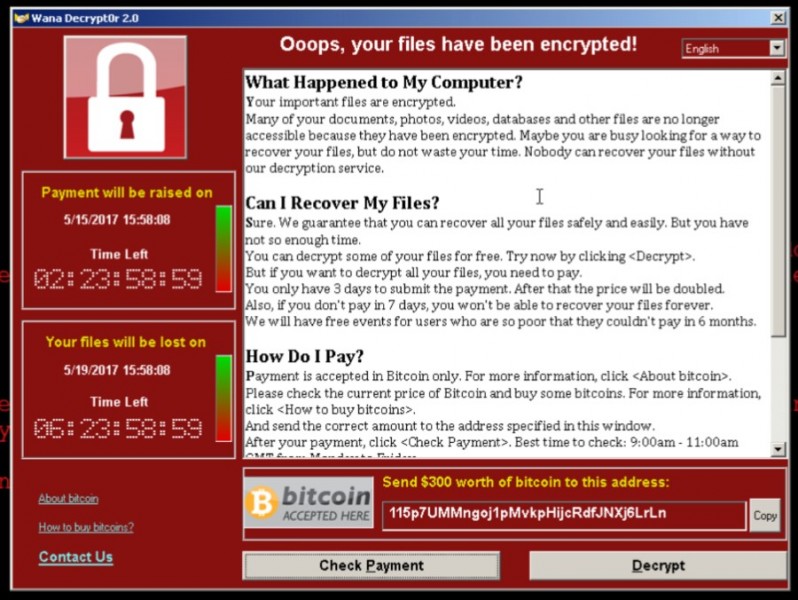
WannaCry is a variant of CryptoLocker. It uses the same cryptography to “password protect” your files that is used on the web for encrypting credit card information. That makes it very difficult to regain access of your files without paying the ransom.
What’s special and therefore dangerous about WannaCry is that it doesn’t just rely on people opening malicious attachments or visiting infected websites. Instead, it just needs access to a computer network. Once in, it spreads like wildfire. It gets in due to a subtle programming problem with Windows file and printer sharing. You will likely have read that the weakness was originally discovered by the USA’s National Security Agency (NSA) who controversially kept it secret for use by them to attack suspects computers. Secrets are all fine until they’re out. This leaked and suddenly all the world’s attackers became aware of the issue before Microsoft did themselves.
Microsoft released a patch to fix the problem in March which should be automatically installed on the majority of computers within a few days however some people, such as the NHS have automatic Windows Updates turned off, may not realise Windows Update is not working properly or are simply running machines too old to receive updates.
WHAT CAN I DO?
The good news is that Windows 10 doesn’t appear to be vulnerable to WannaCry but future variants are likely to try alternative ways, so following good practice is still advisable.
First and foremost, ensure that you have Windows update running and fully up-to-date. Microsoft provides advice how to do this on their website.
Windows Updates are released at least once a month, within the Windows Update program you can view your recently installed updates and should see Microsoft’s “Cumulative Update” that was installed around the 15th March 2017 which provides protection against the bug that WannaCry uses to spread across a network of computers although you can be infected via other means.
If you are running Windows XP, which has been unsupported for a few years now, you should update to a newer version of Windows, however, Microsoft has taken the exceptional step of releasing a one-off update for this issue.
Secondly, ensure your emails and computer in general have a working anti-virus installed. Make sure not to download attachments from emails you don’t recognise.
Thirdly, ensure you have backups which are not accessible on the computer (a zip file of your Documents is no use if it has also been encrypted).
WHAT ARE INFOTEX DOING TO PROTECT ME?
Infotex’s primary website hosting platforms (which hosts over 99% of our client’s websites) runs on servers provided by the Linux operating system which is not affected by this issue so your website hosted by us itself is unaffected. We take security of this platform very seriously and are always happy to discuss measures specific to any client’s environment with them.
Emails processed by Infotex’s Flexidial mail platform has an option, enabled by default, to scan all emails for virus’s and these scanners were updated instantly to protect against email borne copies of WannaCry and will be similarly for future variants. If you want to check that email virus scanning is enabled on your account we’ll be happy to check that for you.