
After 12 years of building websites, I’ve learned something that surprises a lot of business owners: the best-performing sites are never actually finished. They are constantly evolving, adding new features, and getting smarter about how they serve the business.
In spite of this, most businesses treat launch day like crossing the finish line.
A business might launch a beautiful new website — with a clean design, compelling content, and a structure that fits its goals perfectly at the time. It’s a strong foundation and a smart investment. But as the business evolves – with new products, shifting customer needs, or internal changes – the site can slowly drift out of sync. A year later, visitors may struggle to find the right product because the navigation no longer reflects the current offering. Eighteen months on, small inefficiencies such as a lengthy checkout process can start to impact sales. It’s not the original site that failed – it’s just that the business moved forward, and the website didn’t keep up.
The websites that really work for businesses aren’t just maintained – they’re continuously improved with features that solve real problems.
Features such as:
These aren’t just “nice to haves” – they are competitive advantages.

Maybe you have expanded your product range, entered new markets, offer new services or refined how you operate. If your website hasn’t kept pace, it may still reflect where you were, not where you are now.
My husband was recently shopping for motorbike gear on two different sites selling the same brands. One let him filter by jacket type, size, brand, colour, zip length – he found exactly what he wanted in seconds. The other site? Just page after page of scrolling. You can guess which one got his order.
When you started, maybe you were targeting one type of customer. Now you serve three different markets, but your homepage still talks to everyone in the same way. Different landing pages or targeted content could speak to each group properly.
Businesses often think website improvements mean expensive redesigns. But actually small, strategic changes usually beat big redesigns.
So what changes should you make? The answer lies in your website user data.
Once your site is live, you can see exactly how people use it – what’s working, what they’re missing, and where small changes could make things easier. Acting on real user behaviour means you don’t have to guess what to change.
Heat mapping shows where people click. Analytics reveal where they drop off your conversion funnel. User feedback highlights frustration points. This data is incredibly valuable, but only if you make improvements based on it.
The most successful websites are the ones where we regularly review this data and make targeted improvements. This doesn’t require major overhauls, but strategic enhancements applied over time that solve specific problems. Armed with this insight, you can make improvements that keep you ahead of the competition.

Your site doesn’t need every bell and whistle to compete, but don’t let competitors look better than you. If their website is much easier to use, customers will go there instead.
The smart approach? Small updates as you go. Web standards evolve constantly, but incremental improvements beat expensive emergency fixes. Fresh content helps with search visibility. A modern design shows you’re active and credible. Improved navigation will stop people from getting frustrated and leaving.
Small, data-backed improvements will often outperform complete redesigns.
We worked with Stephens Scown Law Firm to build an information hub that pulls together their content – articles, videos, FAQs, and news – organised by legal topics with links to the team members who wrote them. When they posted timely articles about the pandemic, their organic traffic jumped 236% compared to the previous month, then a further 78% the month after.
That’s what happens when you make valuable, relevant content easy to find at exactly the right time.
With Anglian Pumping Services, we redesigned their site and doubled their conversion rate. But more wins came from the ongoing improvements we’ve made since launch: adding smart search to help customers find products faster, implementing click-and-collect services, and integrating with their accounts software to save hours of admin work each week. Each addition solved a real business problem and made their site work harder for them.
Your website works best when it’s treated as a living business tool, not a static digital brochure. That’s exactly what we help businesses do.
We take existing sites and turn them into tools that drive results – whether that’s improving navigation, creating resource hubs, or building features that solve real customer problems.
Talk to us to see how we can help turn your website into something that works harder for your business – exactly where your customers need it most.
Google search results pages continue to evolve. Looking at a search results page today will often look different to a year ago, five years ago and a decade ago. Typically these changes, especially when the search is transactional (someone looking to buy something) have often favoured Google Ads results where businesses pay to see their site placed highly in a text ad or a shopping ad.
The recently introduced AI Overview, where Google uses their Gemini AI to provide an answer at the very top of the search results page now appears in many searches. Recent data suggests that AI in Search is having a drastic impact on question or informational searches which were once more organic results, without paid ads bearing down on them. It’s likely that these AI Overview’s could be impacting businesses more than users switching to ChatGPT for their research, as the AI Overview doesn’t link through to your website.
Here is a quick rundown of some of the elements on a Google results page:

These are the non-paid listings and are based on Google’s algorithm assessing the relevance and authority of your webpage. This is where a blog / news / article strategy can help your business giving you the opportunity to provide highly relevant information to your target audience like these from some of our clients: planning permission considerations, wedding trends and the difference between indemnity and liability.
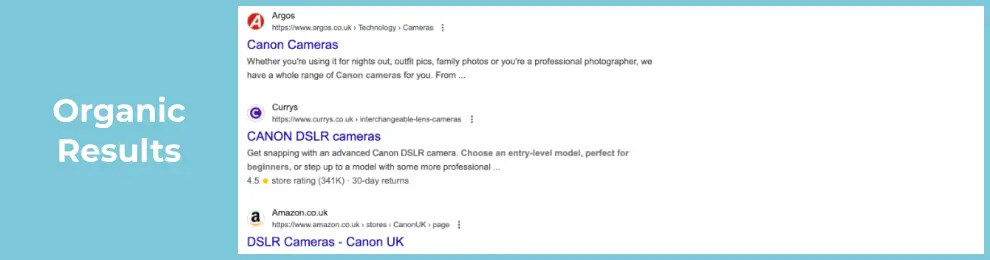
Displayed at the top or bottom of the results page, these ads are marked as “Sponsored” and are typically used for transactional searches to promote products or services and are often a quick way to traffic and leads. Often starting small, establishing a working metric for cost per sale or cost per lead allows you to scale up once you’ve proven the channel.
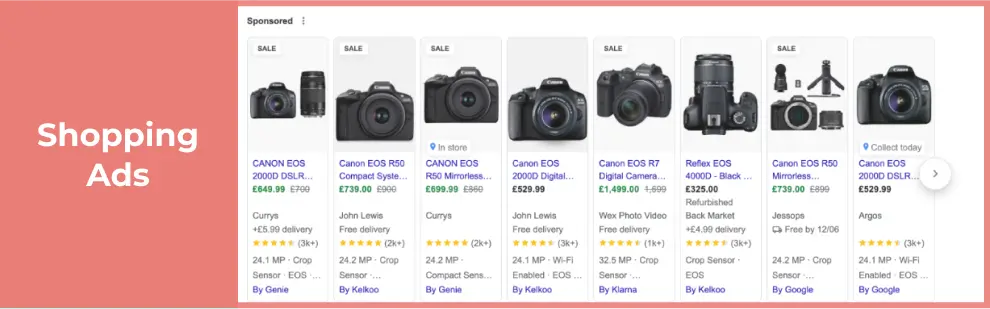
These visual ads showcase your ecommerce products with images and importantly price. These can be a great way to show your catalogue and pre-qualify some of the traffic reaching the site by showing both the goods and the price of the goods before someone clicks.
A relatively new feature (one year ago) that provides an AI-generated summary directly in the results. It’s hard to measure the impact by being in these results as it doesn’t guarantee a click and users may just read the information and be satisfied by the answer.

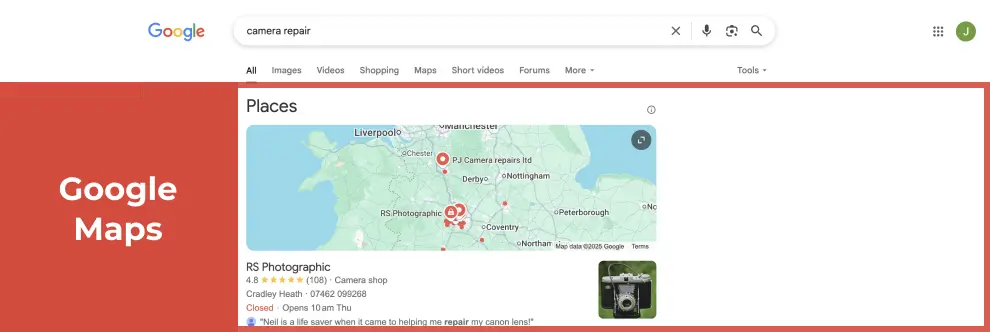
For businesses with a physical presence and serving customers at their location, a Google Maps listing can help you with local traffic displaying images, location, opening hours and reviews in the results page.
Overall, to succeed you will need a broad search strategy and not to rely on any one type of search result, especially as the ground is constantly changing. If you’d like to discuss any of the above, get in touch.
Every website needs a little love and care, is yours getting all it needs to help it truly flourish?
What does a care package mean in respect of a website? We see this as having 4 key areas:
Every business and website is unique. While the person, team, or agency that originally designed your site may have done a great job, their expertise could well be focused just on the design. However, maintaining and managing a website over time requires a different skill set – one they may not possess – making them less suited for ongoing support and care.
Just like your business evolves, so should your brand’s online presence. While a wholesale change is sometimes needed, more often than not small tweaks can ensure that you’re reflecting the values and practices of your wider business. These naturally evolve over time along with the markets they serve, just as you get a painter to give your buildings a touch-up periodically, your website should do the same.
The latest generation of automated tools can allow you to analyse the content on your website and ensure that it is on-brand and current in ways that a few years ago would not be cost-effective. Don’t just rely on tooling however, as branding can be intensely personal which is where a skilled and experienced design and copywriting team can help out.
If you are currently managing your site yourself, are you confident that you’re on top of the latest security updates needed for your site? When applying those updates, how do you check that you’ve not broken other vital parts of the site?
The time between a security issue being identified and attackers taking advantage of it is reducing. You need to ensure that relevant patches are being applied in a timely manner.
Security is a big picture and so much more than just applying patches. It has to be holistic, taking in every part of the ecosystem from password choices to server configuration and filtering out malicious requests. There are so many ways that someone, or an automated bot, can attack your website and the Internet will take advantage of any weakness you leave.
Navigating the world of online compliance can feel like a whole new language! Do you even know if your site complies with privacy requirements such as GDPR & PECR (Privacy & Electronic Communications Regulations) or accessibility rules such as WCAG (Web Content Accessibility Guidelines). We speak this language fluently and can provide actionable insights in plain English.

Using marketing platforms? You might need to implement and maintain compliance with systems like Microsoft UET (Universal Event Tracking) or Google’s CMP (Consent Management Platform), which are constantly being updated. Staying compliant with marketing platform requirements, like these is essential for data collection, ad performance, and avoiding legal penalties. Continuous monitoring of policy and technical updates is necessary in addition to constantly evolving your choice of where to place your ads and the audiences to target.
Is your website lightning-fast, especially on mobile? The average load time for a website on a phone is around 9 seconds compared to the 2 seconds average on desktop. There are a number of techniques that can be used to optimise performance for all platforms.
Caching and CDNs (Content Delivery Networks) ensure that the load time is consistently fast for your growing global audience.
Beyond speed, using metrics such as Google’s Core Web Vitals can help to benchmark your visitors’ experience, this is doubly important as these are also used by Google to help rank sites.
Think about making your website do more. On mobile a website can increasingly act as a fully functioning application. Have you considered whether you could use this to help streamline your customer support needs for example?
We’ve been in this business for over 25 years and we pride ourselves on providing long-term stable relationships with our clients. Perhaps the greatest testament to this is the volume of clients who have been with us for 10 years or more. Our continued success is based purely on our client’s success.
Building a new website is an expensive and sometimes risky process. We work with you to identify what’s working and what’s not, ensuring you get the most value from your initial investment.
We are all about creating an effective partnership with our clients and, to this end, every agreement has an ongoing care package. That may be as simple as providing the routine security patches for your content management system, or a more comprehensive package including marketing and development retainers. This principle is true regardless of your chosen technical platform.
We’re also the secret weapon for some of the smartest design and marketing agencies! Some amazing designers and marketeers understand that their focus should be on creating a great, high performing, site. They need a safe pair of hands to whom they can entrust the ongoing work, someone to keep their client happy once the site is live. This allows them to focus on their next design or marketing project.
We can work silently in the background or connect directly with the end client. If required, our experienced designers can add that extra polish to make even the most effective websites truly shine.
Well that all depends but it all begins with a conversation. Let’s discuss your goals and we’ll follow up with an audit to identify the areas needing most attention. Together we’ll create a plan to evolve your website and ensure it continues to be a valuable asset for your business going forward.
A team of 10 Infotex staff members, friends and partners took on the Norfolk Coast Mighty Hike in aid of the fantastic charity MacMillan Cancer Support. This is a 14.5 mile trek across the north coast of Norfolk, from Cromer to Blakeney.
Starting at 8:20 on a sunny Sunday morning, our team departed and shortly after climbed the 50ft Beeston Hill, granting views of a line of walkers in green stretching into the distance.

The just over half marathon distance had over 1,500 participants which at times looked more like a line of ants stretching as far as the eye could see.

The trek took the team through the picturesque town of Sheringham before running parallel to the North Norfolk Railway, complete with a passing passenger train to keep us company.

A pitstop at Weybourne marked the half-way point and having reached this after approx 2.5 hours everyone was quite upbeat and chatty.
However, the next stretch was to test us to our limits! There followed about 3 miles of seemingly never-ending shingle, taking us alongside the turrets of the Muckleburgh Military Collection all the way through to Cley Beach with no break from the sun beating down.


Walking on hot and shifting shingle with the tide lapping at your shoes if you strayed near the shoreline, and the relentless grind of the noise sapped every ounce of energy from the legs with stones in shoes for added discomfort. The marshall’s glib statement when leaving the earlier pitstop of “just follow the shoreline until you see the red building” was ringing in our ears and eventually a red roof appeared like a mirage from the stony banks to then cruelly disappear from sight once more. While many of our team had undertaken practice walks in the run-up to the event none had thought to train on shingle for such a distance and it’s quite different to the sandy paths expected. Even a seal playing in the wash barely lifted the spirits.
By the time we re-grouped in the car park behind the “red building”, emptied stones from our shoes and taken on a much-needed sugar hit and drinks, it was time for the final push. This took us across the somewhat windswept Blakeney Nature Reserve before we were greeted with the 14-mile marker. A final half-mile climb from the Quayside to The Pastures and the finish line was in sight.
We crossed the finish line as a team at 14:09 after almost 6 hours of solid hiking and the glass of cool fizz waiting had never felt so welcome nor the medal so well earned.


Credit must be paid to the staff from MacMillan Events who put this hike on and provided an army of staff who remained cheerful – even when standing in the most wind-swept locations.
The reason we undertook the hike was to help raise funds for MacMillan Cancer Support. With 1 in 2 people in the UK having to deal with cancer at some point in their life it is no wonder that every member of our team had a personal reason for wanting to take on the challenge. The pain in our legs at the conclusion is still a drop in the ocean compared to what those suffering with this horrible disease go through on a day-to-day basis.
We have set ourselves a goal of raising £2,500 and if you feel able to help contribute towards this excellent charity then visit our Just Giving page.
https://www.justgiving.com/team/infotexuk
Thank you so much to those of you who have already donated, we are incredibly grateful for every penny donated towards this wonderful cause.
Editor Note: A huge thank you goes out to the Infotex’ers who took on the challenge of the Mighty Hike: Angie Vale, Ant Agar, Jonathan Smith, John Harman, Jonny Duffin, Matt Adlem and Michael Letley.
On Sunday 11th May 2025, a team of Infotex staff and friends will be putting on their walking boots and taking part in the Macmillan Mighty Hike.
The event covers 14 miles of the north Norfolk coast and raises vital funds for those living with cancer. It will see our intrepid team start in Cromer before heading west through Sheringham, Salthouse, Cley next the Sea before finishing in Blakeney. Although Norfolk is not known for its mountain peaks the terrain isn’t all easy going as it snakes along sandy and shingle beaches that looks to sap energy with each step.
Our team of 10 is aiming to raise £2,500 for Macmillan, helping those affected by cancer, and their families, with essential medical, practical and emotional support.
We would greatly appreciate your donations in supporting this wonderful cause: www.justgiving.com/team/infotexuk

For the past couple of years, AI has grown exponentially with the introduction of OpenAI (ChatGPTs parent company), and it is showing no signs of slowing down with voice search assistance, AI-generated search results snippets in Google searches and so on…
These features have drastically changed how web users search & research online for example many are opting to research holidays, accommodation & itineraries through AI suggestions rather than already existing website pages.
Many users are now less inclined to use search engines for general queries and opt to use ChatGPT, Google Gemini or any other AI software. Visitors can now navigate to websites via this method as it becomes an alternative user journey to the traditional hunt via search engines.
Users can now use their AI prompts to suggest a variety of different options, and the follow up to tailor it to best suit their requirements resulting in a more conversational tone than a simple search and result. For example, a possible request could be “suggest the best holiday destinations in Europe for the summer”, which would result with a number of different holiday destinations. These can then be refined to particular requirements, such as low price, good transport links and near the sea.
Instead of typing “best digital marketing strategies” on Google, a user might ask ChatGPT, “What are the top digital marketing trends in 2025?” and receive a structured response instantly based on different sources of data rather than searching through.
Gemini and Chat GPT process millions of voice searches every day. The conversational tone of voice searches tend to make it longer and more natural e.g., “How do I improve my website’s SEO rankings?” instead of “SEO tips”.
Businesses should now optimise content for voice search by answering common questions in a conversational tone. Make sure your business details are accurate and up to date on Google Business Profile to improve local voice search rankings as a first step.
The rise of AI is fundamentally reshaping online search behaviour. From conversational queries to AI-powered chatbots and visual search, businesses need to adapt their website and digital marketing strategies to remain competitive.
By embracing these AI-driven search trends, businesses can ensure they remain discoverable and relevant in an evolving AI digital landscape.
A 404 error page is something no website visitor wants to see—but that doesn’t mean it has to be a dead end. Instead of a generic “Page Not Found” message, a well-designed and creative 404 page can keep visitors engaged, entertain them, and should guide them back to relevant content. The best 404 pages turn an unfortunate moment into an opportunity to reinforce brand personality and user experience.
Here are some examples of creative 404 pages we love:
American fast food chain Wendys turns an error into a game. Help Wendy make her orders in time by directing her around your screen towards the ingredients whilst avoiding the pink blobs trying to get you.
If you’re into classic computer games, you’ll love hosting and domain provider Kualo’s 404 page, which allows users to take out their error frustrations on space invaders.
Vev allows users to get their creative juices flowing by offering them a blank canvas to doodle on.
Whilst very similar to Vev’s drawing canvas, Left Logic also include a gallery of previous favourite 404 visitor artworks inspiring a hint of competition in users.
Mad allows users to “doodle” using an entire screen of toggle buttons.
It’s not just doodlers being given the opportunity to get creative, RCA Records offers users the chance to make music.
OK, so we’re a little bias with this one, as we created this page. A little animated version of their Woody character rolls in and out of the page. A site search and some key page links means people can navigate to something more useful.
Headspace keep it on brand by inviting users to take their 404 accident as an opportunity to stop, and take a deep breath.
Lego keep it lighthearted with star of the Lego Movie, Emmet, on their 404 page.
Marvel use a variety of different recognisable characters to convey their message.
Disney also use a recognisable character in their more light hearted style.
Pixar follow suit, with an image of a recognisable character and also use that characters tone of voice for their messaging.
Dasthis appeal to Lord of the Rings fans with a witty reference to Mordor.
Whilst Ready to go Survival gives users a choice of where they want to go next, comparing it to Neo’s choice in the Matrix.
Magnt poke fun at users spelling ability with their venn diagram 404 page.
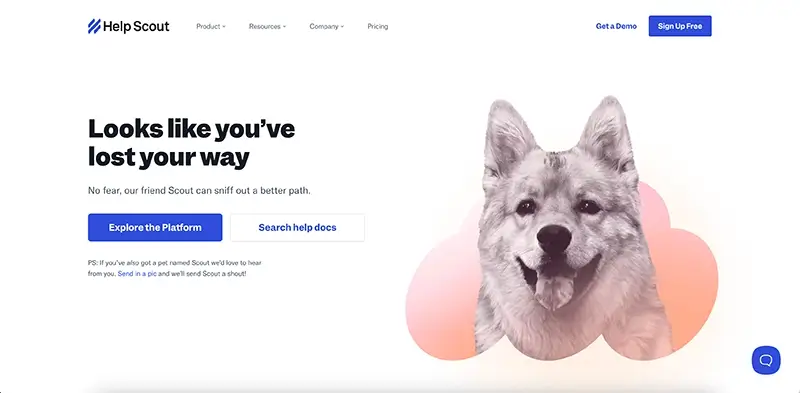
Help scout makes any frustration a user might have felt at their 404 error melt away with their adorable “friend” Scout.
Whilst Amazon seem to have a whole army of different happy pups at their disposal to cheer up frustrated users.
Things get really weird (and wonderful) with Kffein’s 404 page. There’s really no way to explain – you just have to go there yourself…
Self proclaimed as “The most awkward 404 page on the internet” Steve Lamberts way of dealing with an awkward error is to just make things even more uncomfortable with his on page video. Maybe not a choice most people would want on their website – but it’s certainly different.
There are a few really easy tips to avoid visitors seeing too many 404s on your own site:
As the days start to lengthen and it feels like we’re edging out of winter we all look forward to the new life and freshness of spring. Does your website feel the same or is this a good opportunity for a bit of housekeeping to make it spring fresh and ready for the summer?

It is natural in business that staff will periodically move on, either to other roles within your business or elsewhere.
When did you last review the list of users with access to your website’s administration area to ensure that only staff with a current business need have access?
Leaving accounts active for staff no longer employed can lead to severe problems, The British Museum recently had a disgruntled ex-contractor return and use their, still active, access to shut down a number of exhibits ahead of a busy weekend. If their access been revoked promptly they would not have been able to do so. For e-commerce sites you also have a duty of care to the personal data of your customers, per the GDPR legislation.
For WordPress sites, this is as simple as viewing the Users list in the admin and checking that all those under the Administrator, Shop Manager or Editor tabs still need access, and revoking or deleting any who are no longer needed.
From a security point of view you should avoid sharing logins and each staff member should have their own username and unique password for each site.

When did you last change the password for your website admin? Could anyone else know what that password is or is it even in use elsewhere? It is good practice to rotate (i.e. re-generate) passwords periodically to avoid any old record of it escaping your control. Most importantly, ensure that any password you choose is strong and unique, i.e. never re-use the same password on more than one site. Most good password managers have a password generator and if you’re not using a password manager (why not?) then you can still generate a really good password using online tools – WordPress has a strong password generator built in for example.
If you don’t already have 2-factor authentication enabled you may wish to add that to keep your borders fortified.
Websites evolve over time, is yours still showing outdated features or content? Are there still references to COVID-19 precautions or does your contact form still ask for a fax number? All of these things can make your website seem dated and potentially lose business. In some cases, you may even find you have features, and plugins for those, which are no longer relevant and removing these would free up space for more valuable content. Removing redundant plugin(s) can also speed up your website and even make it more secure and easier to manage going forward.
Perhaps it’s time for your website to grow a new feature, some aspect of your business that isn’t already available or something that would make your life easier, it could be anything from a listing of clearance items, a newsletter sign-up form or even a customer management system to allow you to run your business more effectively?

Do you send out newsletters to your customers regularly, if so when did you last check on your bounce rate and interactions, do you need to remove old recipients who’ve not engaged for years (or try to re-engage them), are there new active customers who you’re not sending to that might appreciate your newsletters, is your template on-brand and fitting with your website or a relic from previous seasons?

Are you still running Google Ads campaigns using the same words & phrases as last year? The world moves on and so must your choice of terms to remain relevant and cost-effective rather than old and dusty.
With so many changes to online advertising is your website using the latest types of campaign to get the best conversion rates and lowest cost per lead? Are your landing pages fresh and inviting? A Digital Marketing review might be what you need to clean up your marketing efforts.

Ok, don’t try putting emulsion on your monitor, however your website’s design does age, is yours looking from the last decade? If so it might be time to speak to our designers about adding a bit of pizzazz back into things, and perhaps take that one step further with a full user experience review so that it is spring-fresh, sparkling and doing all it can to drive your business forward.
Gen Z (born 1997-2012) are known as the first true digital natives who have grown up with the internet, having easy access to social media, portable digital devices, smartphones, tablets as part of everyday life. They are tech savvy and highly adept with online digital tools and platforms whose preferred way to communicate is via online messaging through social media, gaming platforms and smartphone apps.
Generation Z has distinct digital behaviours compared to millennials, Gen X and boomers. Due to growing up in a digital online world they have had instant access to information to meet their particular needs preferring short form video engaging interactive content which is easier to digest rather than long form text.
Millenials grew up in the time period of making the transition from analogue to digital devices. Gen Z prefer mobile to desktop having had access to smartphones and portable devices.

There is a trend of Gen Z moving away from Google to using social media for searching for information and discovering new brands.
In a recent study when asked where they most frequently discover new products, 18- to 27-year-old consumers responded with:
This data highlights the growing shift toward social media platforms for product discovery among Gen Z.
However, don’t be fooled as Google isn’t going away anytime soon. Millennials (42.45%), Gen X (41.1%), and Boomers (55.9%) still rely on a Google Search first.
As traditional search marketing and AI evolve brands need to leverage social platforms, embrace authentic marketing, and prioritize experiential content to thrive with Gen Z.
I have always felt that a lot of business software development misses a very important part: a structured and formal approach to the business rules and requirements of the developed system (the business Domain). I have always felt that there was never really a home for it, or at least I was not sure where it should go; front-end developers tend to mix it with interface concerns, database experts tend to put it in the database, and newcomers have no idea where to put it. As more requirements and features are added to the same code base over time, what we end up with is an unmanageable and confusing mess, often referred to as a big ball of mud.
This approach to software development will introduce errors because it is difficult or impossible to properly test. It degrades developer productivity because bugs are very hard to pin down even when their results can be observed, because it is not obvious where to look. Any added functionality will create an even bigger ball of mud as there is no incentive to not do so. Eventually the software solution becomes unmanageable.

Where appropriate, we follow a Domain Driven Design approach. The Domain components of the solution model the processes and requirements of the actual real-world business processes and requirements. This is done in focused and specific modules that relate to a particular business context – in this way, each module focuses on a specific aspect of the overall solution and does not try and do too much.
These models contain both properties – the current state of the model, and methods – the ability to change the model state through actions. The state of the model should not be externally editable except through these methods and should never become invalid – if an attempt is made to change the model into an invalid state (through a method) that change should fail with the reason. In this way we enforce the business rules of the application.
This works well, and I believe this is especially important for business software, as, often, the requirements will contain lots of complicated business logic, rules and invariants and perhaps state-mandated regulations like GDPR. By attempting to distil this into a single, well-defined layer of the application, it becomes easier to test, easier to maintain and much easier to reason about. Additionally, because the domain model components resist becoming invalid, it should be much more robust and more difficult to break (either intentionally or by accident).
We can then build on and out from the domain components, adding database access and external services, and expose the domain to any software systems that require its services.
There is no such thing as a free lunch – on the flip side, this highly structured software engineering takes much more discipline and consideration. It also requires belief and confidence in the process from all involved and therefore can increase the time and effort it takes to initially deliver the system.
In our 25+ year history we have moved our headquarters several times to meet the changing needs of the business. From a smaller ground floor office to a much larger two floored premises as our team and client needs grew. However, despite relocating we’ve always remained true to our roots, basing ourselves within the Woodbridge area. The town has recently been voted the happiest place to live in Britain and our loyalty and connection to the local area certainly attests to that.

Like many organisations during Covid, we closed our office and decided to be entirely remote based, giving us time to take stock and see how the post-covid world would unfold. During this time we were fortunate enough to have use of the fantastic facilities at Martley Hall and Riduna Park, enabling us to still have face to face meetings and work together in person when the need arose.
Fast forward to 2024 and we felt it was time to have our own base once again, having established a new routine and way of working we needed a smaller premises to offer hybrid working, a place to host client meetings and our company-wide gatherings.

We found this and more at our new premises on TideMill Way, less than 5 minutes walk from the train station and Woodbridge town centre. With stunning views of the River Deben, fab coffee from Suffolk Coffee Pod and relaxing walks right on our doorstep to get the creativity flowing. Our new home feels like we’re in a holiday destination rather than an average office block – arguably our best office yet!

Towards the end of each year the audio streaming platform Spotify releases its Spotify Wrapped data analysis. Whilst at first glance it provides an individual user with certain claims to fame and insights on the way they’ve listened to music or podcasts that year, it also highlights the sheer volume of information that Spotify have recorded in their data platform.
In an article published in April 2024 Spotify stated that they are processing 1.4 trillion data points every day. Those would include plays of particular tracks or podcasts, subscriptions to podcasts, likes of tracks and even searches for a particular song or artist. Spotify have built their own bespoke data platform to support this volume of activity because the insights it gives into how users interact with their product helps them to further enhance their service.
Spotify are very open about the way they record, store and analyse the data they collect with their engineering team having their own website at engineering.atspotify.com where they post information about their use of data. Each of those 1.4 trillion data points is recorded in their event delivery infrastructure which feeds into the data platform where the data is processed and stored. Spotify is an extremely data-driven organisation, they use the data platform to report on their own key performance indicators and to improve their product whilst also making it available to users through in app recommendations and in the more fun Spotify Wrapped.
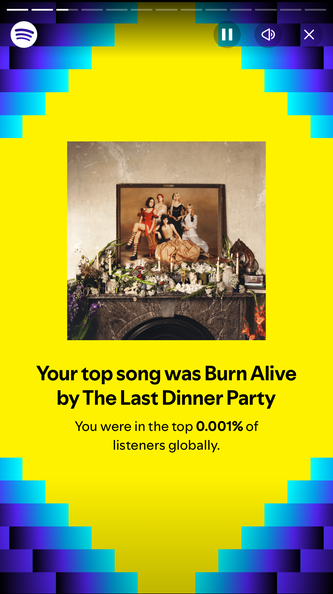
Let’s look at a few insights from members of the Infotex team in their 2024 Spotify Wrapped. One person found themselves in the top 0.001% of users listening to a particular track – achieved by listening to it 166 times.
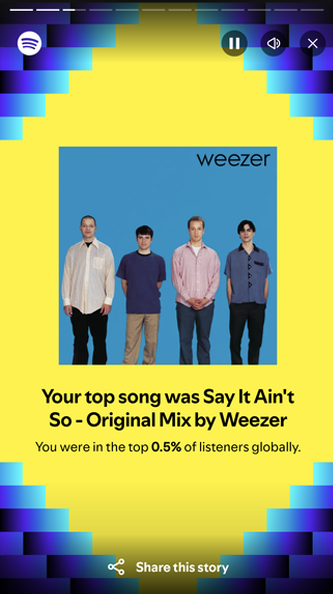
Not all songs required a high number of listens to get into the top listeners category. It only took 3 listens to get into the top 0.5% of listeners of this Weezer track.
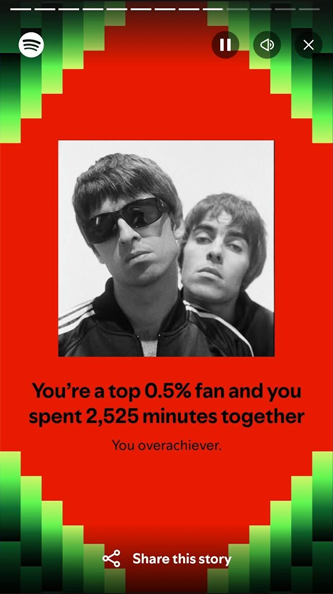
One Oasis fan found themselves in the top 0.5% of listeners for that band this year, kick started after their reunion tour announcement.
This year Spotify have decided to theme some of their insights, one user found their October listening described as a Heist Happy Rock Britpop month:
If you want to see the most popular artists, songs, albums, audiobooks and podcasts across the world you can visit Spotify’s Newsroom for the details.
Discover how our team can help you on your journey.
Talk to us today